Ensure the port number in the “Port” box matches the port number the SSH server requires. SSH servers use port 22 by default, but servers are often configured to use other port numbers instead. Click “Open” to connect. You’ll see a security alert the first time you try to connect to a server. If you ever have a web server (or other type of server) running on a remote Linux box, and you want to connect to it using your local system, here’s how you do it. Ssh-i./.ssh/key.pem-N -L 8081:localhost:8000 user@host. This reads as: Authenticate using a key. The port you’re listening on on your local system is localhost:8081. Nov 05, 2020 If you have access to a remote SSH server, you can set up a remote port forwarding as follows: ssh -R 8080:127.0.0.1:3000 -N -f user@remote.host. The command above will make the ssh server listen on port 8080, and tunnel all traffic from this port to your local machine on port 3000. By default the SSH daemon on a server runs on port 22. Your SSH client will assume that this is the case when trying to connect. If your SSH server is listening on a non-standard port (this is demonstrated in a later section), you will have to specify the new port number when connecting with your client. You can do this by specifying the port. By default, SSH runs on port 22. A port is simply a communication endpoint where a process is routed once it arrives on a server. To connect through SSH, a user requires the port number (e.g. 22 in this case) and a public IP address of the server alongside a username and a password.
- Ssh Server For Windows Download
- Ssrs 2014 New Features
- Ssh Server Port Ubuntu
- Setup Ssh Port Forwarding
Security always plays a major role on the internet: That’s why the SSH security procedure is firmly anchored in the TCP/IP protocol stack. The SSH protocol allows users to establish a secure connection between two computers. The network protocol has been in use since 1995 and has been revised several times since then. We explain the most important terminology of the SSH protocol and how encryption works.
- An explanation of how SSH works
The shell is the part of the operating system that allows users to access the computer. Normally this is the text-based command line (or command prompt, terminal, or console), but the graphical user interface is also called a shell. The method of establishing a connection is called ‘secure shell’ because the protocol creates a secure connection to the shell of another computer.
What do you need SSH for?
SSH enables two computers to establish a secure and direct connection within a potentially unsecure network, such as the internet. This is necessary so that third parties can’t access the data stream, which would result in sensitive data falling into the wrong hands. Even before secure shell, there were ways to establish direct connection between two computers, but the corresponding applications such as Telnet, Remote Shell, or rlogin were all unsecure. SSH encrypts the connection between two computers and enables a second one to be operated from one computer.
SSH not only provides an encrypted connection, but also ensures that only connections are established between the designated computers (i.e. no man-in-the-middle attack is possible) and that the corresponding data cannot be manipulated on its way to the recipient. The remote computer has always been accessed via the command line. They are used to send commands to the remote device. However, it is now also possible to use virtual network computing (VNC) to mirror a graphical user interface (which is not always available on servers) to your own computer and therefore control the other computer.
SSH has many different areas of application:
- Managing servers that cannot be accessed locally
- Secure transmission of files
- Secure creation of backups
- Connection between two computers with end-to-end encryption
- Remote maintenance from other computers
The development of SSH has also influenced other protocols. For example, the unsecure FTP protocol, which is used to download files to and from a server, has been further developed into the SSH file transfer protocol (SFTP).
An advantage of SSH is that the protocol runs on all common operating systems. Originally a Unix application, it is also implemented on all Linux distributions and macOS. But SSH can also be used on Windows, if you install a relevant program.
SSH vs. OpenSSH
Secure shell was originally created in 1995 as an open source project. In the same year, however, the developer Tatu Ylönen founded a company that developed the protocol further. Therefore, the initially open project developed more and more into a proprietary software. However, the network community did not accept this and developed an open split based on the SSH-1 protocol: OpenSSH. However, since SSH community security is also continuing to work on secure shell, two competing protocols now exist side by side. There is the proprietary SSH-2 protocol (a further development, since security vulnerabilities were found in SSH-1) and OpenSSH.
OpenSSH and commercial SSH are relatively similar when it comes to functionality and scope. The difference is mainly with the cost and the support. If you choose the SSH communication security product, you will also receive 24/7 support. This can be particularly useful for large companies with alternating IT managers. OpenSSH, on the other hand, offers the advantage of an open source community, meaning that the project is constantly being developed further by many participants.


An explanation of how SSH works
Secure shell uses multiple encryption and authentication techniques. On the one hand, this ensures that data streams cannot be read or manipulated. On the other hand, only authorized participants can contact each other.
Authentication
The first step is that the SSH server and client authenticate themselves to one another. The server sends a certificate to the client to verify that it is the correct server. When making contact, there is the risk that a third party will get between the two participants and therefore intercept the connection. Since the certificate itself is also encrypted, it cannot be imitated. Once the client knows what the correct certificate is, no third parties can contact the relevant server.
After server authentication, however, the client must also identify itself as being authorized to access the server. A password can be used for this purpose. This (or the encrypted hash value of it) is stored on the server. As a result, users must enter their password each time they log onto the different server during the same session. For this reason, there is an alternative method of client-side authentication using the key pair public key and private key.
The private key is created individually for your own computer and secured with a passphrase that should be longer than a typical password. The private key is stored exclusively on your own computer and always remains secret. If you want to establish an SSH connection, just enter the passphrase and you will gain access to the private key.
There are also public keys on the server (just like on the client itself). The server creates a cryptographic problem with its public key and sends this to the client. The server then decrypts the problem with its own private key, sends the solution back, and informs the server that it is allowed to establish a legitimate connection.
During a session, you only need to enter the passphrase once to connect to any number of servers, At the end of the session, users should log off from their local computers to ensure that no third party with physical access to the local computer can connect to the server.
Encryption
After mutual authentication, the two communication participants establish an encrypted connection. To do this, a key is generated for the session, which expires when the session is over. This is not to be confused with the public/private key pairs, which are only used for key exchange. The key used for symmetric encryption is only valid with this one session. Both client and server have the same key, so any messages that are exchanged can be encrypted and decrypted. Client and server create the key simultaneously, but independently of one another. In the so-called key change algorithm, both parties use certain public and secret information to create the key.
Another form of encryption takes place in SSH through hashing. A hash is a form of signature for the transmitted data. An algorithm generates a unique hash from the data. If data is manipulated, the hash value changes automatically. This way the recipient can know whether data has been changed by third parties along the way. The hash values are designed in such a way that they cannot be easily simulated. It’s not possible to create two different transmissions with the same hash – this is known as collision protection.
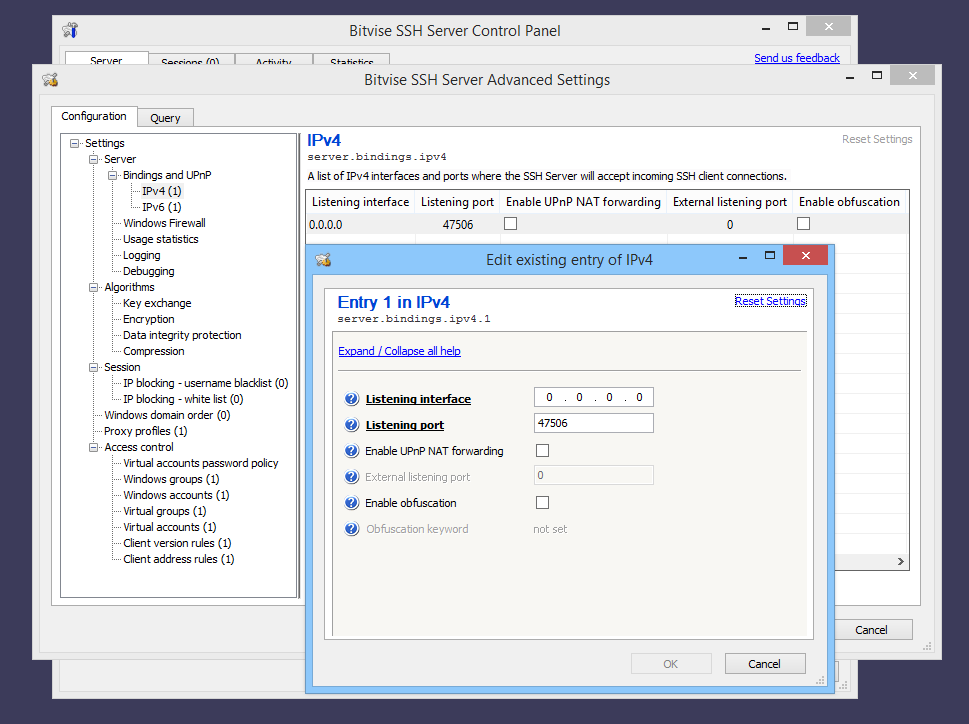
SSH ports
TCP ports are endpoints that open servers and clients to enable communication. As with a port, the communication partners receive and send the data packets via these ports. TCP has an address space of 16 bits and therefore 65535 ports are available. However, the internet assigned numbers authority (IANA) has assigned a number of ports (exactly 1024) for certain applications, including the SSH port. By default, all SSH connections run on port 22.
Since the port that SSH connections pass through is widely known and transmits sensitive data, the SSH port is a favorite destination for cybercriminals. Therefore, some users think it makes sense to relocate the SSH port. However, this only offers short-term protection. With a port scanner, it is possible to find any ports used by a computer.
With SSH, port forwarding is also possible: The SSH port of a client or server is used by another participant within a local network to create a secure connection via the internet. The participants create a tunnel for this: The data is received via port 22 and then forwarded to the client in the local network.
SSH clients
The SSH client is usually your own PC that you want to use to establish a connection to the server. To achieve this, you can or must (depending on the operating system) install separate software that establishes an SSH connection. These programs are also usually called SSH clients. The fee-based Tectia SSH comes from SSH communication security and additionally contains a server software. But there are also numerous free alternatives, such as the open source software, PuTTy for Windows and Linux, or lsh, which works on all operating systems based on Unix.
Some programs provide users with a graphical interface that simplifies the configuration and deployment of SSH. In principle, secure shell can also be executed from the command line – even without further installation on macOS and other Unix operating systems.
SSH server
The SSH server is the counterpart to the client. The term is also used here for the software. Much of the client software also works on servers. In addition, there is software designed exclusively for SSH servers. It is normal to start SSH on servers when you start up the computer. This guarantees that you can access the server from outside at any time via SSH.
Strictly speaking, it isn’t necessary for the SSH server to be located in a remote data center. Users can also install an SSH server on their own PC at home to benefit from the advantages of port forwarding, for example.
Security always plays a major role on the internet: That’s why the SSH security procedure is firmly anchored in the TCP/IP protocol stack. The SSH protocol allows users to establish a secure connection between two computers. The network protocol has been in use since 1995 and has been revised several times since then. We explain the most important terminology of the SSH protocol and how encryption works.
- An explanation of how SSH works
The shell is the part of the operating system that allows users to access the computer. Normally this is the text-based command line (or command prompt, terminal, or console), but the graphical user interface is also called a shell. The method of establishing a connection is called ‘secure shell’ because the protocol creates a secure connection to the shell of another computer.
What do you need SSH for?
SSH enables two computers to establish a secure and direct connection within a potentially unsecure network, such as the internet. This is necessary so that third parties can’t access the data stream, which would result in sensitive data falling into the wrong hands. Even before secure shell, there were ways to establish direct connection between two computers, but the corresponding applications such as Telnet, Remote Shell, or rlogin were all unsecure. SSH encrypts the connection between two computers and enables a second one to be operated from one computer.
SSH not only provides an encrypted connection, but also ensures that only connections are established between the designated computers (i.e. no man-in-the-middle attack is possible) and that the corresponding data cannot be manipulated on its way to the recipient. The remote computer has always been accessed via the command line. They are used to send commands to the remote device. However, it is now also possible to use virtual network computing (VNC) to mirror a graphical user interface (which is not always available on servers) to your own computer and therefore control the other computer.
SSH has many different areas of application:

Ssh Server For Windows Download
- Managing servers that cannot be accessed locally
- Secure transmission of files
- Secure creation of backups
- Connection between two computers with end-to-end encryption
- Remote maintenance from other computers
The development of SSH has also influenced other protocols. For example, the unsecure FTP protocol, which is used to download files to and from a server, has been further developed into the SSH file transfer protocol (SFTP).
An advantage of SSH is that the protocol runs on all common operating systems. Originally a Unix application, it is also implemented on all Linux distributions and macOS. But SSH can also be used on Windows, if you install a relevant program.
SSH vs. OpenSSH
Secure shell was originally created in 1995 as an open source project. In the same year, however, the developer Tatu Ylönen founded a company that developed the protocol further. Therefore, the initially open project developed more and more into a proprietary software. However, the network community did not accept this and developed an open split based on the SSH-1 protocol: OpenSSH. However, since SSH community security is also continuing to work on secure shell, two competing protocols now exist side by side. There is the proprietary SSH-2 protocol (a further development, since security vulnerabilities were found in SSH-1) and OpenSSH.
OpenSSH and commercial SSH are relatively similar when it comes to functionality and scope. The difference is mainly with the cost and the support. If you choose the SSH communication security product, you will also receive 24/7 support. This can be particularly useful for large companies with alternating IT managers. OpenSSH, on the other hand, offers the advantage of an open source community, meaning that the project is constantly being developed further by many participants.
An explanation of how SSH works
Secure shell uses multiple encryption and authentication techniques. On the one hand, this ensures that data streams cannot be read or manipulated. On the other hand, only authorized participants can contact each other.
Authentication
The first step is that the SSH server and client authenticate themselves to one another. The server sends a certificate to the client to verify that it is the correct server. When making contact, there is the risk that a third party will get between the two participants and therefore intercept the connection. Since the certificate itself is also encrypted, it cannot be imitated. Once the client knows what the correct certificate is, no third parties can contact the relevant server.
After server authentication, however, the client must also identify itself as being authorized to access the server. A password can be used for this purpose. This (or the encrypted hash value of it) is stored on the server. As a result, users must enter their password each time they log onto the different server during the same session. For this reason, there is an alternative method of client-side authentication using the key pair public key and private key.
The private key is created individually for your own computer and secured with a passphrase that should be longer than a typical password. The private key is stored exclusively on your own computer and always remains secret. If you want to establish an SSH connection, just enter the passphrase and you will gain access to the private key.
There are also public keys on the server (just like on the client itself). The server creates a cryptographic problem with its public key and sends this to the client. The server then decrypts the problem with its own private key, sends the solution back, and informs the server that it is allowed to establish a legitimate connection.
Ssrs 2014 New Features
During a session, you only need to enter the passphrase once to connect to any number of servers, At the end of the session, users should log off from their local computers to ensure that no third party with physical access to the local computer can connect to the server.
Encryption
After mutual authentication, the two communication participants establish an encrypted connection. To do this, a key is generated for the session, which expires when the session is over. This is not to be confused with the public/private key pairs, which are only used for key exchange. The key used for symmetric encryption is only valid with this one session. Both client and server have the same key, so any messages that are exchanged can be encrypted and decrypted. Client and server create the key simultaneously, but independently of one another. In the so-called key change algorithm, both parties use certain public and secret information to create the key.
Another form of encryption takes place in SSH through hashing. A hash is a form of signature for the transmitted data. An algorithm generates a unique hash from the data. If data is manipulated, the hash value changes automatically. This way the recipient can know whether data has been changed by third parties along the way. The hash values are designed in such a way that they cannot be easily simulated. It’s not possible to create two different transmissions with the same hash – this is known as collision protection.
SSH ports
TCP ports are endpoints that open servers and clients to enable communication. As with a port, the communication partners receive and send the data packets via these ports. TCP has an address space of 16 bits and therefore 65535 ports are available. However, the internet assigned numbers authority (IANA) has assigned a number of ports (exactly 1024) for certain applications, including the SSH port. By default, all SSH connections run on port 22.
Since the port that SSH connections pass through is widely known and transmits sensitive data, the SSH port is a favorite destination for cybercriminals. Therefore, some users think it makes sense to relocate the SSH port. However, this only offers short-term protection. With a port scanner, it is possible to find any ports used by a computer.
With SSH, port forwarding is also possible: The SSH port of a client or server is used by another participant within a local network to create a secure connection via the internet. The participants create a tunnel for this: The data is received via port 22 and then forwarded to the client in the local network.
SSH clients
The SSH client is usually your own PC that you want to use to establish a connection to the server. To achieve this, you can or must (depending on the operating system) install separate software that establishes an SSH connection. These programs are also usually called SSH clients. The fee-based Tectia SSH comes from SSH communication security and additionally contains a server software. But there are also numerous free alternatives, such as the open source software, PuTTy for Windows and Linux, or lsh, which works on all operating systems based on Unix.
Some programs provide users with a graphical interface that simplifies the configuration and deployment of SSH. In principle, secure shell can also be executed from the command line – even without further installation on macOS and other Unix operating systems.
SSH server
The SSH server is the counterpart to the client. The term is also used here for the software. Much of the client software also works on servers. In addition, there is software designed exclusively for SSH servers. It is normal to start SSH on servers when you start up the computer. This guarantees that you can access the server from outside at any time via SSH.

Ssh Server Port Ubuntu
Strictly speaking, it isn’t necessary for the SSH server to be located in a remote data center. Users can also install an SSH server on their own PC at home to benefit from the advantages of port forwarding, for example.
Setup Ssh Port Forwarding
