Azure Multi-Factor Authentication Server (Azure MFA Server) can be used to seamlessly connect with various third-party VPN solutions. This article focuses on Cisco® ASA VPN appliance, Citrix NetScaler SSL VPN appliance, and the Juniper Networks Secure Access/Pulse Secure Connect Secure SSL VPN appliance. We created configuration guides to address these three common appliances. Azure MFA Server can also integrate with most other systems that use RADIUS, LDAP, IIS, or claims-based authentication to AD FS. You can find more details in Azure MFA Server configurations.
The CERT Coordination Center at Carnegie Mellon University announced last week that Cisco AnyConnect 4.7.x and prior store session cookies insecurely in memory. LANCOM Systems, and pfSense. Cisco AnyConnect Woes Sorry to ask this slightly blindly, but has anyone had issues using Cisco AnyConnect SSL-VPN behind pfSense firewall? I've got a fresh out of the box config with pfSense and once I connect to my employer's anyconnect client, I can no longer access any public site via DNS.
Important
As of July 1, 2019, Microsoft no longer offers MFA Server for new deployments. New customers that want to require multi-factor authentication (MFA) during sign-in events should use cloud-based Azure AD Multi-Factor Authentication.
To get started with cloud-based MFA, see Tutorial: Secure user sign-in events with Azure AD Multi-Factor Authentication.
If you use cloud-based MFA, see Integrate your VPN infrastructure with Azure MFA.
Existing customers that activated MFA Server before July 1, 2019 can download the latest version, future updates, and generate activation credentials as usual.
Cisco ASA VPN appliance and Azure MFA Server
Azure MFA Server integrates with your Cisco® ASA VPN appliance to provide additional security for Cisco AnyConnect® VPN logins and portal access. You can use either the LDAP or RADIUS protocol. Select one of the following to download the detailed step-by-step configuration guides.
| Configuration Guide | Description |
|---|---|
| Cisco ASA with Anyconnect VPN and Azure MFA Configuration for LDAP | Integrate your Cisco ASA VPN appliance with Azure MFA using LDAP |
| Cisco ASA with Anyconnect VPN and Azure MFA Configuration for RADIUS | Integrate your Cisco ASA VPN appliance with Azure MFA using RADIUS |
Citrix NetScaler SSL VPN and Azure MFA Server
Cisco Vpn Pfsense
Azure MFA Server integrates with your Citrix NetScaler SSL VPN appliance to provide additional security for Citrix NetScaler SSL VPN logins and portal access. You can use either the LDAP or RADIUS protocol. Select one of the following to download the detailed step-by-step configuration guides.
| Configuration Guide | Description |
|---|---|
| Citrix NetScaler SSL VPN and Azure MFA Configuration for LDAP | Integrate your Citrix NetScaler SSL VPN with Azure MFA appliance using LDAP |
| Citrix NetScaler SSL VPN and Azure MFA Configuration for RADIUS | Integrate your Citrix NetScaler SSL VPN appliance with Azure MFA using RADIUS |
Juniper/Pulse Secure SSL VPN appliance and Azure MFA Server
Azure MFA Server integrates with your Juniper/Pulse Secure SSL VPN appliance to provide additional security for Juniper/Pulse Secure SSL VPN logins and portal access. You can use either the LDAP or RADIUS protocol. Select one of the following to download the detailed step-by-step configuration guides.
| Configuration Guide | Description |
|---|---|
| Juniper/Pulse Secure SSL VPN and Azure MFA Configuration for LDAP | Integrate your Juniper/Pulse Secure SSL VPN with Azure MFA appliance using LDAP |
| Juniper/Pulse Secure SSL VPN and Azure MFA Configuration for RADIUS | Integrate your Juniper/Pulse Secure SSL VPN appliance with Azure MFA using RADIUS |
Next steps
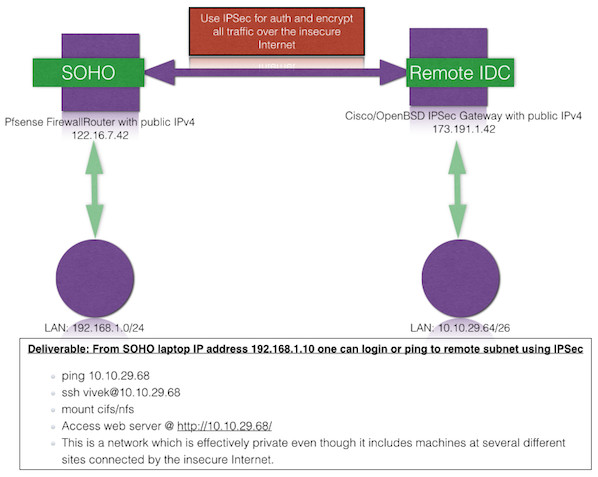
This page describes how to configure IPsec to connect pfSense® routerand a Cisco IOS router with IPsec capabilities.
Example Network¶
This diagram shows the specifics of the network where this VPN is beingconfigured. For the sake of this documentation, both hosts were onprivate subnets, but functionally equivalent to two hosts across theInternet.
Configuring the router¶
First, configure the phase 1 settings with a crypto isakmp policy. Thefollowing sets it for 3DES, SHA and group 2 to match the pfSenseconfiguration shown later.
Next, configure the pre-shared key. The key in this example is ABCDEFG,but be sure to use something random and secure for any productiondeployments. 10.0.66.22 is the WAN IP of the pfSense system beingused.
Next configure the transform set for phase 2. This uses ESP, 3DESand SHA. The transform set is named 3DES-SHA, which is how it willbe referred to later.
Now configure an access list that will match the local and remotesubnets on the pfSense router. This is configured as access-list 100,which will be used in the next step. Remember this uses wildcard masks,so a /24 network (255.255.255.0 mask) is represented as 0.0.0.255.
Now configure the crypto map for this VPN:
Lastly, under the interface configuration for the interface where theVPN will terminate (the one with the public IP), assign the crypto map:
The configuration is then finished on the Cisco side.
Configuring pfSense Software¶
This screenshot shows the pfSense configuration matching the above Ciscoconfiguration.
In the above example, the pfSense IPsec tunnel should be set as follows:
Phase 1:
Remote Gateway: 10.0.64.175Authentication Method: Pre-Shared KeyNegotiation Mode: MainMy Identifier: My IP AddressPre-Shared Key: ABCDEFGEncryption Algorithm: 3DESHash Algorithm: SHA1DH Key Group: 2Lifetime: 28800NAT Traversal: Disable
It may also be advisable to set Proposal Checking to Obey to avoidsome issues with building a tunnel when the other side initiates.
Phase 2:
Mode: Tunnel IPv4Local Network: LAN SubnetRemote Network: 172.26.5.0/24Protocol: ESPEncryption Algorithm: 3DES (others may also be checked, but besure to leave 3DES checked)Hash Algorithm: SHA1PFS Key Group: 2Lifetime: 3600

Testing the connection¶
To test the connection, from the pfSense router, do the following:
Navigate to Diagnostics > Ping
Enter an IP address on the remote network
Choose the LAN interface
Click Ping.
The initial negotiation may make all three of the first pings timeout,so try it a second time as well. If configured as depicted above, oncethe tunnel connects, the following will be seen:
Troubleshooting¶
Cisco Anyconnect Vpn Software Download
If the connection doesn’t come up, there is a mismatch somewhere in theconfiguration. Depending on specifics, more useful information may beobtained from pfSense router or the Cisco router. Checking logs on bothends is recommended. For pfSense software, browse toStatus > System Logs on the IPsec tab. For Cisco, rundebug crypto isakmp and term mon (if not connected via serialconsole) to make the debug messages appear in a session. The outputcan be verbose, but will usually tell specifically what was mismatched.
“No NAT” List on Cisco IOS¶

It may also be necessary to tell Cisco IOS not to NAT the traffic thatis destined for the IPsec tunnel. There are several ways to accomplishthis, depending on how the router has NAT configured. If the followingexample does not help, there are several examples that turn up in aGoogle search for “cisco ios nonat ipsec”:
Cisco Anyconnect Windows 10
This will direct the router to prevent NAT if the traffic is going fromthe subnet behind the Cisco router to the subnet behind the pfSenserouter, but allow it in all other cases.
